openec2 Article Description
Part 5
Configure an SES/S3 Bucket for forwarding email
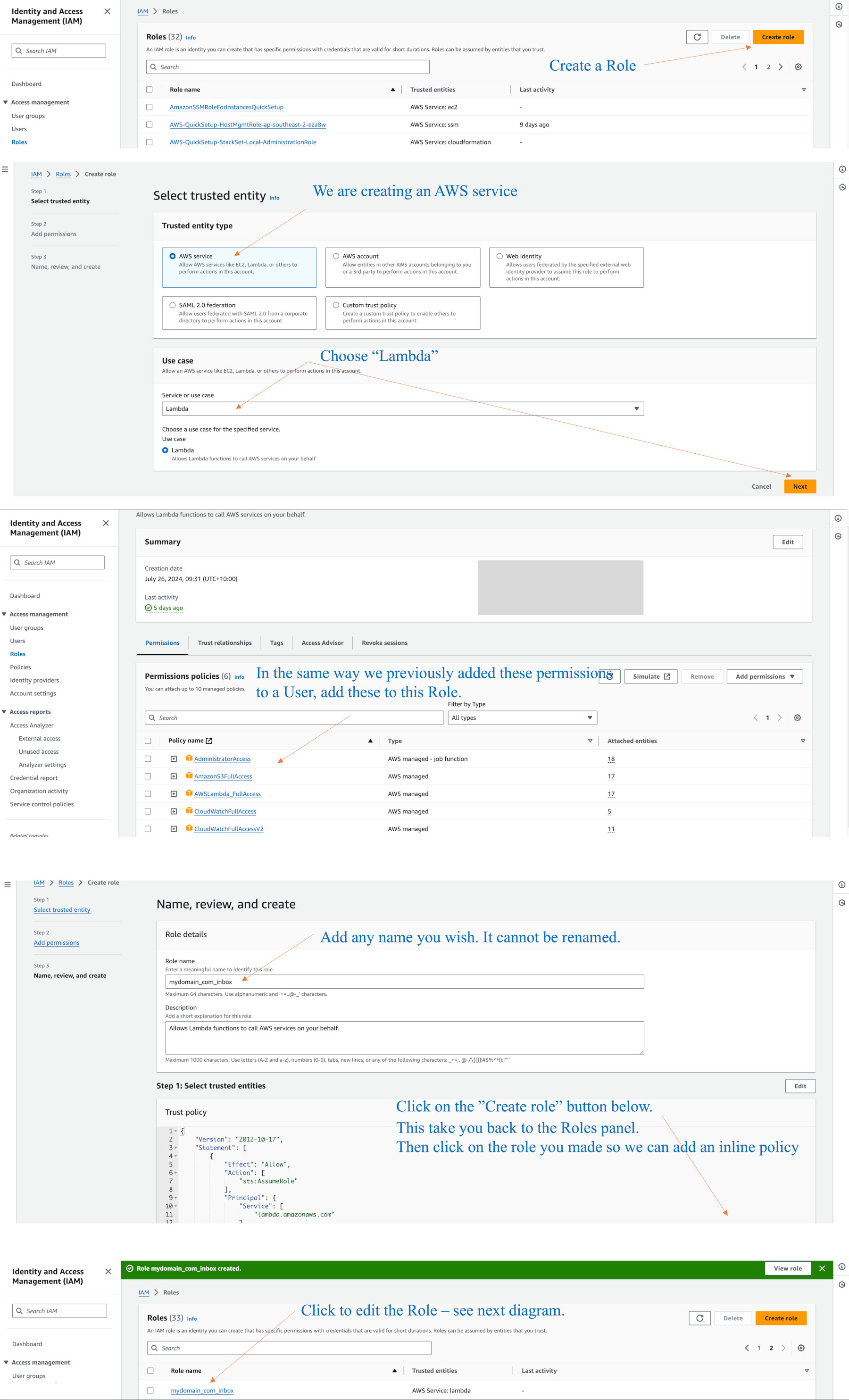
We will create an IAM Role that gives us ability to create a Lambda function using our S3 email bucket. This Lambda function will be added to our SES default receiving rule we previously made.The AIM role will link specifically to the bucket, which in our example is mydomain.com.inbox. (It can be any name you created.)
Go to the IAM console > Roles > “Create Role” button.
The Trusted entity type is Amazon service. From the Use case menu, select Lambda, then Next.
As you see in the screenshots below, basically throw everything at it. You have learnt how to add these items in a previous lesson when adding an IAM User. While creating this role, you will need to give it a name of your choosing.
Add tehse to the role: AdministratorAccess, AmazonS3FullAccess, AWSLambda_FullAccess, CloudwWatchFullAccess, and V2.
We will come back to adding our own policy in a moment.
Click “Add Role”.
Go back to the main Role panel and find the new role, then click on it so we can add a policy.
On the right you will see a small pop-down menu, “Add permissions”. Click on the submenu item called “Create inline policy”.
On the next panel, from the Select a service menu, choose S3. Then you will see more options. Click the checkbox “Manual actions > All S3 actions”.
On the Policy editor at the top, click on the JSON tab.
Using your own bucket name, add these lines, then click Next.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"logs:CreateLogGroup",
"logs:CreateLogStream",
"logs:PutLogEvents"
],
"Resource": "arn:aws:logs:*:*:*"
},
{
"Effect": "Allow",
"Action": "ses:SendRawEmail",
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:PutObject"
],
"Resource": "arn:aws:s3:::YOUR_EMAIL_BUCKET_NAME/*"
}
]
}
Use your own bucket name, such as mydomain.com.inbox above where it says YOUR_EMAIL_BUCKET_NAME.
On the next panel you give this a name. You cannot edit names later.
Click on the “Create policy” button. This takes yo back to the policy screen where you see your inline policy has been added. If you made a type, the editor should tell you, but you can edit the JSON at any time.
The Role will now be used to create a Lambda function in your email region, e.g. Oregon.
The next lesson will add the above content to SES Receiving rules, so we may forward emails that arrive in the S3 bucket.